Ever wondered what is dark web?, What is tor? Dark web is one of the mostly heard word but most of people don’t know what is dark web and how to access dark web. People doesn’t have deep knowledge about browsers for dark web surfing and how to access dark web safely or what is tor browser.
So, today I am going to make you clear everything about Dark web. We will talk about every thing like what is dark web? How does dark web operates , how to access dark web safely, what is tor browsers or browser to use for dark web and much more.
Note: DOn’t use the knowledge you got from here in illegal acts. I will not be held responsible for your acts.
If you want to learn about creating free lynda premium account then click here.
What is dark web?
Dark web is the collection of all websites which operates in dark corner of the internet. In simple words it isn’t only related with website’s but anything related to the interconnection of virtual things by secured anonymized network. Such websites can be accessed using secure, anonymised connection called tor network. Dark websites run like any other web server on internet like creator of site creates web server and user access it but difference is first the web traffic of user passes through tor network.
Users sends request of something to website and the user requests first passes through tor network through the maze like encrypted structure and then only website gets the request of user. When the websites get request they don’t know the real IP address of users. Web servers only know return address of tor network. Web servers sends response back to tor network from where the response is again passed to user. Due to this user can access any site anonymously as website owners can’t find who is trying to access the website.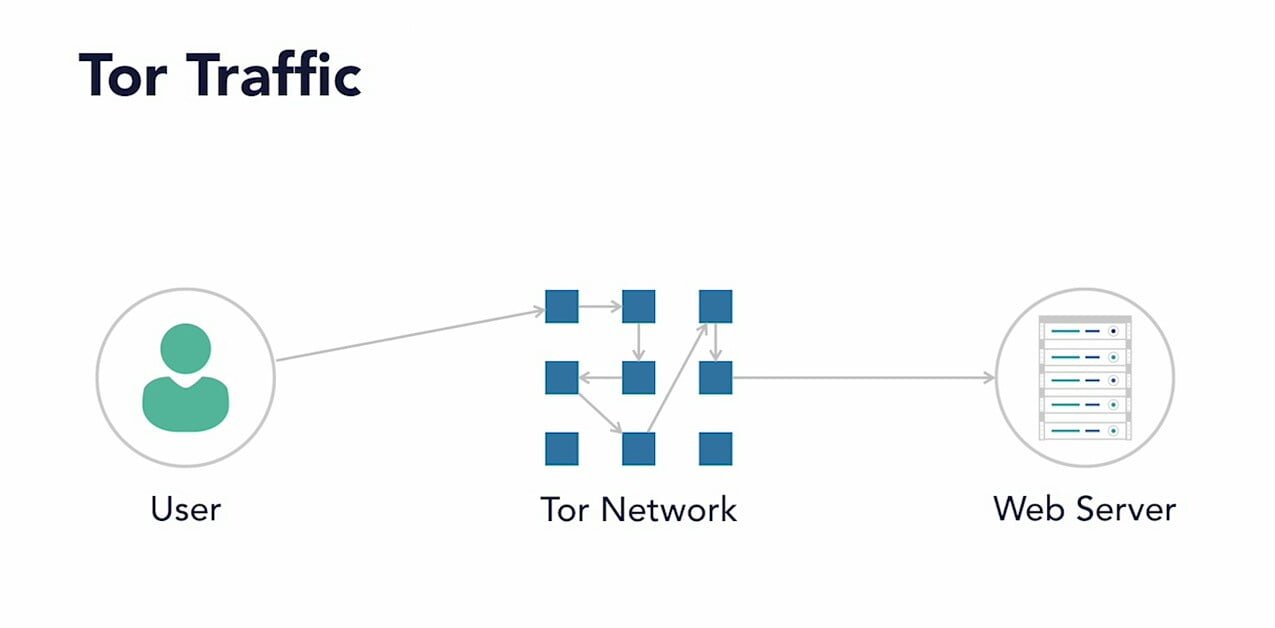
Users can access hidden sites which are only available on tor network or dark web. Such sites are hidden so users can’t find real owners of website and web owners can’t find who is accessing the site. Due to this it is quit popular among criminals and dissident groups.
Benefits of tor network or dark web
- Users can access normal websites anonymously.
- Site owners can host hidden sites anonymously.
- Users can get data which they can’t get on regular web or web browsers.
- Every hidden sites on internet can be accessed in anonymous manner.
Who created dark web? History of tor network or dark web
Onion routing which made dark web possible was originally developed in United states’s government laboratory. A team of mathematicians and computer scientists first created this concept in 1990s in US Naval Research Laboratory. They were using it as medium to protect government communication. One of the scientist Paul siberson tried to create the prototype of tor browser and the Naval Research Laboratory released his code under the free license in 2004 launching tor browser in public.


After it’s wide spread it was necessary to create it’s own organization so, Tor foundation was born. It attracted many donations from private sectors or organizations and from government agencies. Every personal or organization involved in creation of Tor network was funded by US government which shows government agencies are using tor network for their communication with their agents on different fields.
Tor users are increasing rapidly nowadays due to it’s advantages. From my point of view i can’t say tor doesn’t leaks information to the US government because it is mostly funded by US government. This kinds of rumors can be seen nowadays. It’s only my point of view so, it might also not be true.


Cryptographic or encryption is basis of tor
Cryptography is an important factor in any information protecting sectors. In simple language cryptography is related with converting readable text into code like encrypted form. Encryption protects the unnecessary and unauthorized disclosure of sensitive information in public. Security function of tor network also depends on cryptography.
What is cryptography?
The use of mathematical algorithms to transform information into an encrypted form that is not readable by unauthorized individuals is cryptography. Cryptography does provide authorized individuals ability to transform it back into readable form through decryption using various mathematical algorithms.
Cryptography depends on two process encryption where plaintext are encrypted into unreadable version called ciphertext and other process is decryption where such encrypted ciphertext are converted into readable form.
Encryption algorithms works just like mathematical algorithms. A simple text goes under series or mathematical algorithms which are complex in nature. They are encrypted or converted into code like ciphertext form which are complex in nature and can’t be converted back without access to decryption key used in encryption. Keys are like password. If we try to read the encrypted text without decryption key then they are nothing but mathematical garbage for us.


Decryption algorithms are like encryption algorithm’s but they work in reverse manner. Ciphertext or encrypted text are moved through series of mathematical algorithms to convert into readable text. Key is must for decryption for performing correct operations. 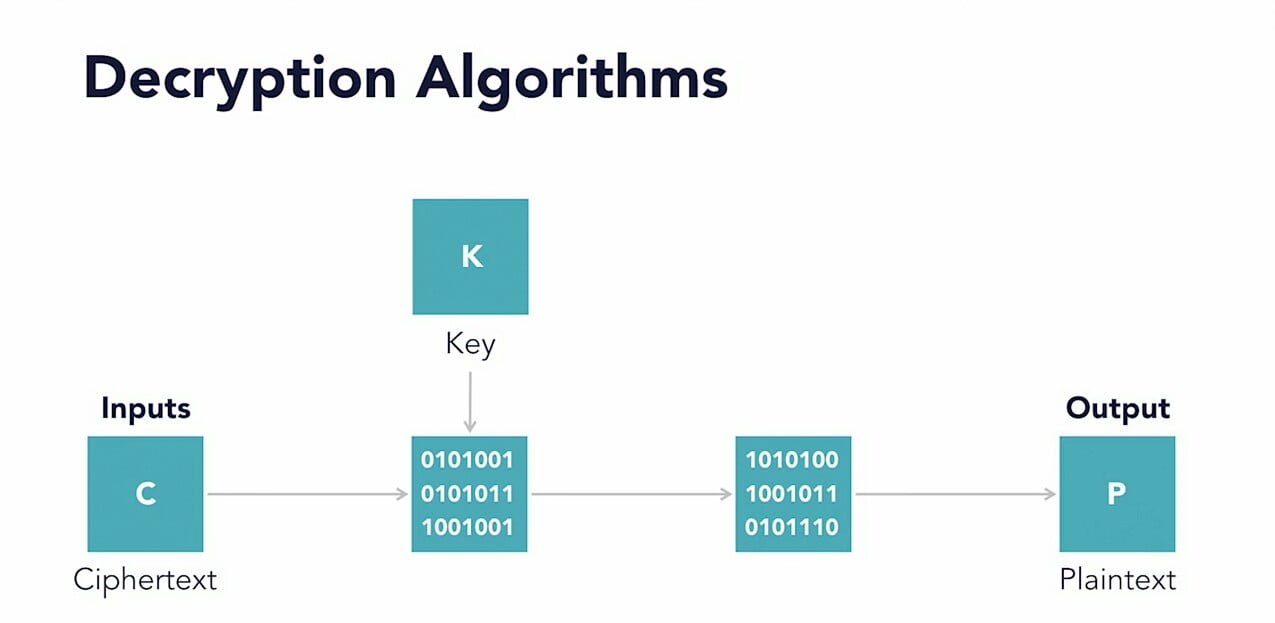


What is symmetric algorithm?
Symmetric algorithm in cryptography means using same algorithm for encryption and encryption. If i use ‘Roshan’ for encrypting data then i must use ‘Roshan’ for decrypting data too in symmetric cryptography. 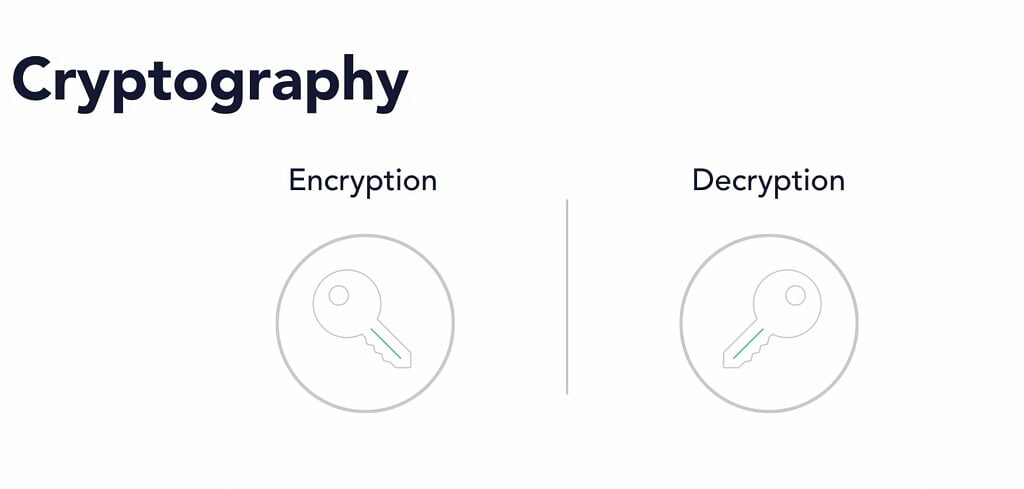


Let’s take an example. Taylor and swift are two different persons. To convert encrypted or coded message between them they can use a same key. Key work like password to convert code into readable form. But if third person john came between them then they require different keys to convert different encrypted text between three of them. Between taylor and swift, between swift and john, between john and taylor a different password like that in symmetric cryptography.
Larger groups requires more keys. This formula calculate the number of keys required for an organization to encrypt in symmetric cryptography:
n(n-1)/2 , where n is number of people involved. See this chart to see how much keys we require in symmetric cryptography!


What is asymmetric algorithm?
In asymmetric cryptography we use different keys for encryption and decryption.


To solve the problem of requirement of large number of keys in symmetric cryptography we use asymmetric cryptography. Two keys are used in this cryptography for each person. They are public and private keys.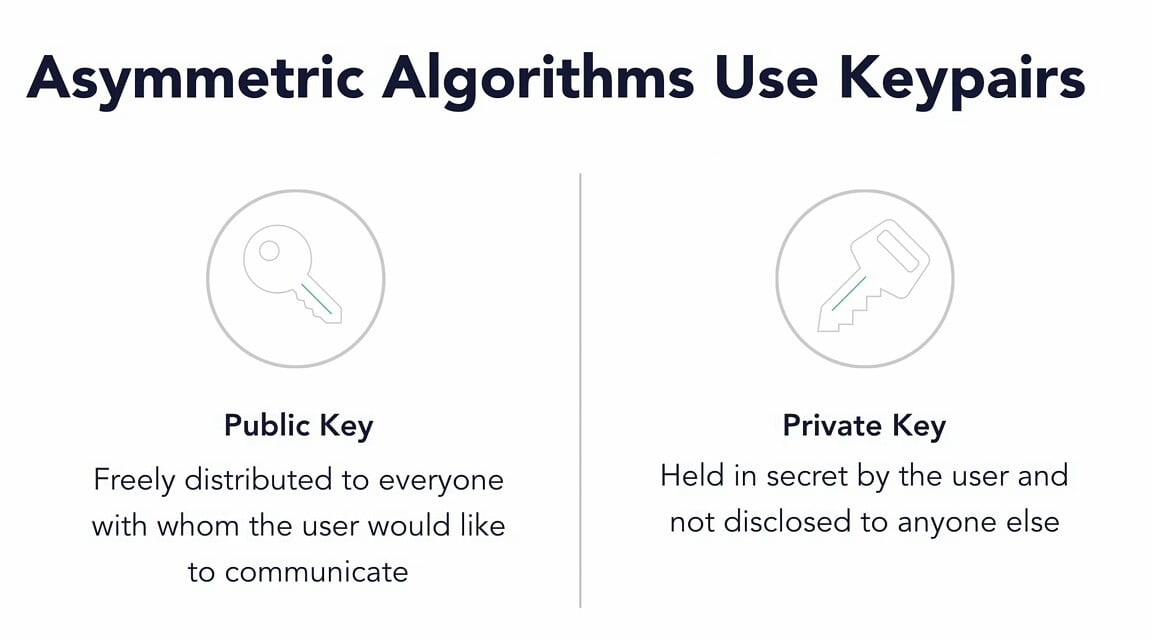


see this chart in difference of keys required between both cryptography.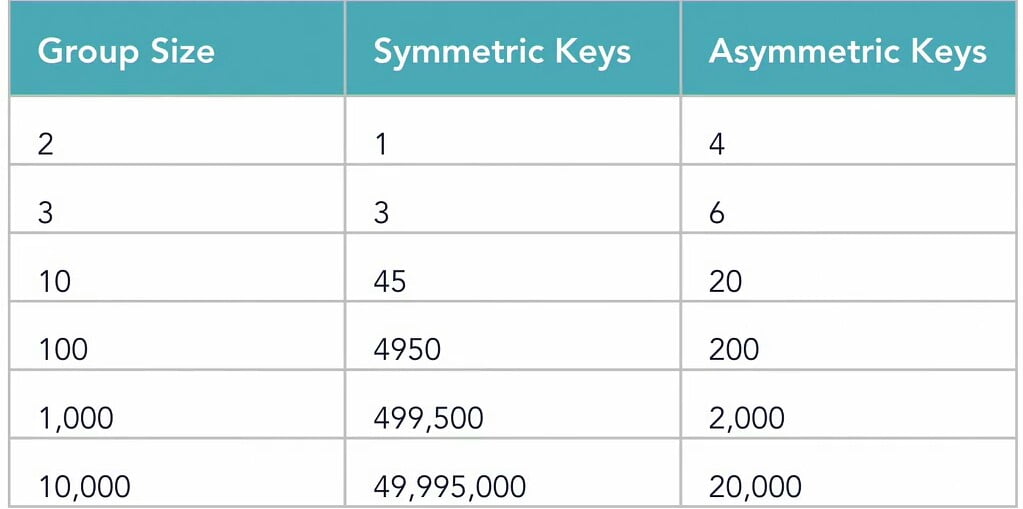


Picture credit goes to real owner!
Join our telegram group by clicking here
That’s it for this part of our article about what is dark and what is tor. In our next article we will learn how to access dark web and using it anonymously and safely. In this article we learned in detail about what is dark web, History of dark web, cryptographic or encryption in dark web or tor. This information are valuable information which can’t be easily available on internet. Hope you got cleared on some aspects of dark web. Goodbye till our next post about how to access dark web.





No Responses