You might have heard about doxxing or doxing. Some of you might not have heard a bit about it but what does doxing mean? Thinking what is doxing? Doxing is related simply to methods applied by hackers to find details of their target and also by police or law enforcement to get details about criminals. How do they do doxing? Let’s learn about it today.
Being a cybersecurity journalist I am quite familiar with the way security officers and hackers do doxing. I want to share with you some of the information on what does doxing mean and how it is done by police and by hackers.
What does doxing mean?
Doxing or doxxing is a technique of tracing someone or gathering information or details about an individual using the various sources available on the internet. Word ‘doxing’ is derived from ‘documents’, ‘docs’. It entirely depends upon the ability of an individual to gather information and recognize even a tiny bit of information as valuable and use it in his/her benefit. Using various sources and data, leaked information, etc available on the internet, you can find personal details of a person. So, doxing someone is quit popular among hackers and law enforcement. It’s like, the more you know about your enemy, the easier it becomes to find his/her flaws.
remember that doxing someone is illegal and we are not responsible for what you do.
How police and hackers find details about someone
Well, police and hackers have their own way to dox someone but they have lots of common way. Police can check on their database about criminal’s profiles or in other databases bided by law but hackers don’t have such access. If the police don’t have a record in their databases or files then the way they perform is similar to hackers.
You can design a doxing template according to the information you want. The basic format of data or details you need to acquire to dox someone is given below:
- Personal information
- Name:
- Date of birth:
- Phone number:
- Email:
- Facebook:
- Youtube:
- Twitter:
- Skype/Instagram
- Other:
2. Additional information
- Picture of an individual:
- IP Address:
- Hobbies:
- Friends:
- Other:
3. House address
- Address:
- City:
- State:
- Zip:
- Country:
- Occupation:
- Other:
4. Information about family member(Optional)
- Name:
- Date of birth:
- Occupation:
- Email:
- Phone number:
- Picture:
- Facebook:
- Other:
This is a template that you fill by doxing someone. You can dox someone according to the information you needed. For hackers above information will be enough for doing fraud activities and for law enforcement, those information will be enough to identify and pull out someone.
If you want to learn about getting a virtual credit card (VCC) for free then click here
Doxing technique used by hackers and police
You might be cleared about what does doxing mean until now. Doxing someone is illegal in most of the country. So, everything you do is upon you. Let’s discuss some basic techniques of doxing which you can do.
- Doxing with Skype
Skype is one of the first steps in doxing someone. You can get the IP address of the user easily. If your target is on Skype, this is the first step you must do.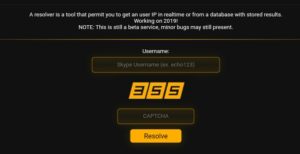
You can use https://cyber-hub.pw/ to resolve skype. Cyber-hub is the best website out there. You can also use other skype resolver tool or skype grab tools by googling. Just enter the username and you can get the IP Address of the user.
After you get the IP Address of the user, just go to ip-tracker.org and enter the IP Address. Now you get the location of the user. This is quite a starting from just a skype username. You can lookup in Cyber-hub, leaked database of skype about the username and get valuable information like email and phone number.
2. Doxing with email and getting email
When it comes to getting emails, Facebook is one of the best options out there. Just search your target name and try to find his/her Facebook. If you got successful, to find Facebook account, create a Facebook account using yahoo and send the target friend request. If their information like email is public then you can easily get.
After your friend request gets accepted you can go to www.facebook.com/invite_history.php after signing in and see contact details like phone number and email of your target.
Skype is also the best method to find the email which I have described in the upper method.
You can also import your target contact info from yahoo after creating Facebook account using it. Just create your yahoo account and click on import contact information from Facebook. This is quite an easy method.
What to do if we already have an email? If so, then just do reverse steps. Open Facebook in browsers like UC browser. Click on forget password and search the email. You will get a Facebook account with a photo of your target.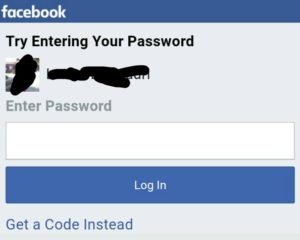


These are few sites to do back check if you have got the target email.
- com.lullar.com
- www.emailfinder.com
- www.spokeo.com/email-search
You can search for database leaks for that email. See if any account associated with that email was ever leaked. I will describe this down.
3.Doxxing with phone number
How to start if you have got a target phone number? Just go to the sites given below and search phone number according to country.
- www.reversemobile.com/index.php/
- www.thisnumber.com
- www.whitepages.com
- www.dgs.dk (Denmark)
- www.canada411.ca (Canada)
- www.goyellow.da/ (Germany)
You can also go to facebook.com in UC browser and go to forget password and search phone number. This way you can get facebook account where you can get lot’s of information. Try to search in skype, add contact too.
Finding social media
You can use given sites to get the target’s social media information. Just enter the email address to get information.
- pipl.com
- thatsthem.com
- com.lullar.com
- namechk.com
- email.addresssearch.com
4. Doxing with name
Using people name who are above 18, you can get information about them. It requires lot’s of time. Just go to below site and search. Nowadays Facebook is quite used for this.
- www.whitepages.com
- pipl.com
- www.thatsthem.com
- www.yellowpages.com
- www.ratsit.se/BC/SearchPerson.aspx/ (Sweden)
- find-person-germany.com (Germany)
- www.dgs.dk (Denmark)
- www.peekyou.com/united_kingdom
5. Doxing with IP Address and getting IP Address
If you have IP Address of the target then search in ip-tracker.org or infosniper.net, proxyornot.com and get location information. You can also search your target’s IP Address like “127.0.0.1” on google and you might find some information.
Suppose you have got access to contact the target. In such case go to grabify.link . There just enter some URL of photo or interesting topics and shorten it. Send it to your victim using some catchy title. When you victim clicks it you can go back to grabify.link and get the IP Address of the target.
6. Doxing using friends/alias
Suppose your target has name like Mike Tyson. In such case you will get 1000’s of results. In such case you can use target alias name and search it if it is unique. Like if you target alias name is Yagami then you can search Yagami in media’s like Facebook and get target alias account. Under that account you can get information about your target account.
7. Doxing using Paypal
You can get lots of information like name, address, email from Paypal. If your target use Paypal then just click on request or send money in target email. There you can get their name.
This method can be used according to the payment system or apps used according to the country. You can enter your target email or phone number on send or request money option and get their name. 


8. Grabbing House Information
This will be easy when you have address of your target. You can simply search on google maps address and get house details. You can also use the sites given below. Just submit the images file you have on target which you find on social media’s or any other sites in the sites given below with the URL and you can get the location of the image.
- geoimgr.com
- exifdata.com
If your target is on USA and you have the address of target then you can use the sites given below.
9. Doxing with database leak
You can use the site given below to check if any account related to your target email was leaked in any database leaks or breaches.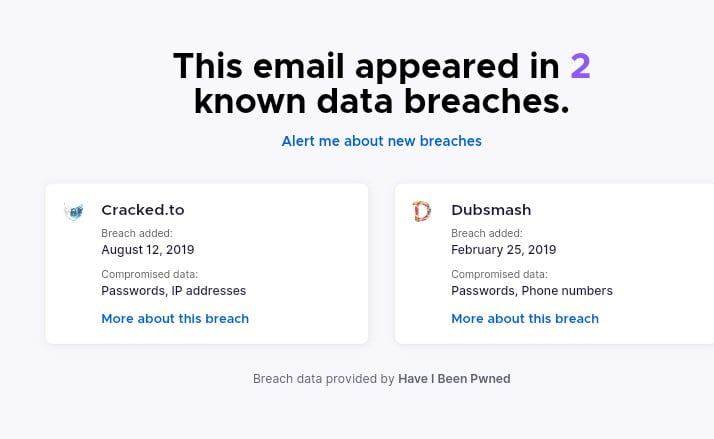


- leakedsources.ru
- snusbase.com
- haveibeenpwned.com
- monitor.firefox.com
Now you can search about that leaked database on exploit-db.com or anywhere on internet. Just search about your target info in that leaked database. You can also use hacking forums.
10. Reverse lookup image
You can basically upload the image you have on your target and upload on a website called tineye.com . Here you can find if the image Is uploaded anywhere before. This reverse image lookup is quite an advance method you can follow.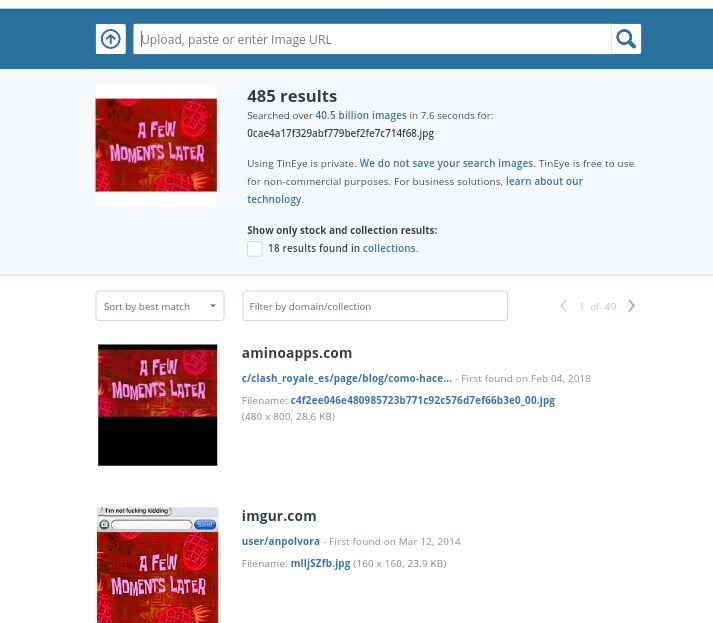


Some useful links to get information
Dox release
- https://skidpaste.com/
- https://pastebin.com/
- https://paste.org/p/home/
- https://paste4btc.com/
Website Information lookup
- https://who.is/
- https://whois.com/
IP Address track
- https://mostwantedhf.info/
- https://www.ip-tracker.org/
- https://ipaddress.com/
Picture search
- exifdata.com
- geoimgr.com
- images.google.com
- www.ctriq.org/google/images/
Username lookup
- www.google.com/advanced_search
- checkusernames.com
- pipl.com
- knowem.com
Passwords lookup
- hacked-emails.com
- haveibeenpawned.com
- breachalarm.com
Phone information lookup
- www.spydialer.com/default.aspx
- www.fonefinder.net
- www.reversemobile.com
- www.phonevalidator.com/index.aspx
- thatsthem.com
Other
- www.ussearch.com
- www.peoplefinders.com/criminal-records
USA Person lookup
- www.anywho.com
- www.intelius.com
- https://www.whitepages.com
- www.peoplefinders.com
- www.publicrecords.directory
- www.skipease.com
- www.411.com
- www.411locate.com
- www.zabasearch.com
- www.vetfriends.com
- www.nuwber.com
- www.addresses.com
- www.yellowpages.com
- www.radaris.com
- www.advancedbackgroundchecks.com
- www.spokeo.com
- www.superpages.com
UK Person lookup
- www.britishphonebook.com
- www.peekyou.com
- www.webmii.com
- www.gov.uk/electoral-register/overview
- www.yasni.com
- www.192.com
Canada person lookup
- http://www.freeality.com/finde.htm
- www.canada411.ca
Technique to prevent someone from doxing you
Upto now you might be cleared about what does doxing mean. The best way to prevent someone from doxing you or getting information about you is to dox yourself and remove the information leaks about you. After learning how someone like law enforcement or hacker dox, you can simply reverse use it to remove information about you on the internet. I will give you some basic techniques.
- Hiding IP Address
This is simple to do. Just use proxy or VPN. Don’t use free VPN or proxy service and always use browser like firefox and brave.
2. Removing Dox
You can dox yourself and try to remove your traces. This is quite simple. Just contact the site where data about you appears and contact them to remove it. You can contact google on support.google.com/legal/troubleshooter/1114905 and ask them to remove. This will be long process but is quite effective.
3. Secure transactions
Use bitcoin for transactions. This keeps your identify secured.
4. Encrypted emails
You can use email service providers like protonmail and tutanota.com . They are secured to use.
5. Messaging service
Use Discord, XAMPP, Telegram which are far more secured and helps to keep your identity safe.
That’s it for our article about doxing. Now you might be cleared about what does doxing means. Don’t get confused with spelling of doxxing and doxing because both are same. If you have any query on what is doxxing or doxing then feel free to contact us. Yet more interesting articles, tutorials, hacks and tricks are to be learned and share. The long journey is still waiting for us. Stay updated, support us and we will grow together, learn together.





No Responses