(Updated on September, 25, 2024)
What is a botnet? If you have ever wanted to learn every concept of what is botnet then this post is for you. We will learn everything about botnet and how to set up botnet. Premium knowledge will be provided for free in this post. I will try to explain it in as much detail as I can. Let’s learn what is botnet.
What is a botnet?
Botnet can be definied as the network of infected computers. A botnet is a collection of internet-connected devices, which may include PCs, servers, mobile devices, and internet of Things devices that are infected and controlled by a common type of software called malware. Users are often unaware of a botnet infecting their system. In basic language, bots are programs that are automated or you can say robotic. In a simple context, bots refer to those computers which can be controlled from the external source which is programmed in them.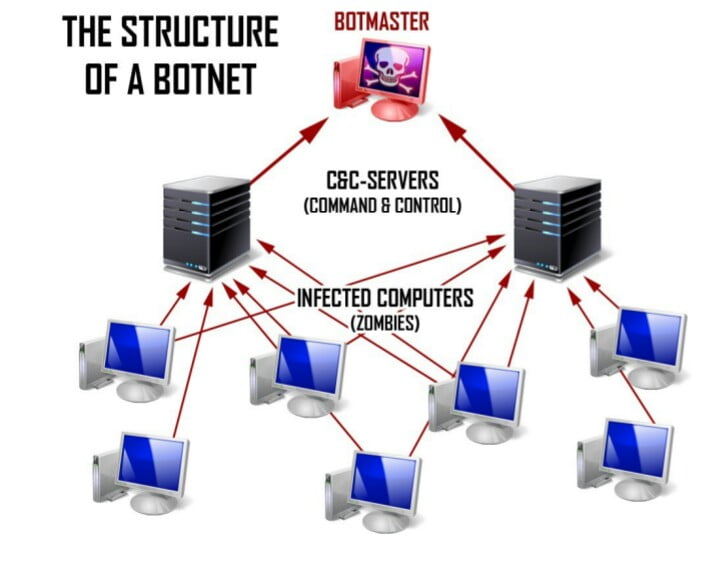
Now, the attacker gains access to the victim’s computers through a virus or any miscellaneous code. Most of the time computers are operating normally, so the malicious operations which are running in their device stay hidden from the user. Infected devices are controlled remotely by threat actors, often cyber criminals, and are used for specific functions. Now you might have some concept of what is a botnet. Botnets are even sold in deepweb for various purposes. It is widely used in illegal activities which we don’t promote to do.
What are botnets used for?
We learned what is a botnet. But what is botnet used for? Botnets are widely used for many purposes. Let’s learn some of the things botnets are used for.
- Generate malicious traffic for distributed denial-of-service attacks(DDOS)
- Cryptocurrency mining
- Surveillance
- Stealing data, etc, and many other things.
Type of botnets:
- IOT(Internet of things)
The Internet of things (IOT) is the network of physical devices, vehicles, home appliances, and other items embedded with electronics, software, sensors, actuators, and network connectivity which enables these objects to connect and exchange data.
Mirai is a malware that turns networked devices running Linux into remotely controlled “bots” that can be used as part of a botnet in large-scale network attacks. It primarily targets online consumer devices such as IP cameras and home routers. The Mirai botnet was first found in August 2016. - IRC (Internet Relay Chat)
Internet Relay Chat (IRC) is an application layer protocol that facilitates communication in the form of text. The chat process works on a client/server networking model and bots are controlled by IRC Server. - RAT (Remote Access Trojan)
RAT is a specific type of malware that controls a system via a remote network connection as if by physical access. While desktop sharing and remote administration have many legal uses, RAT is usually associated with criminal or malicious activity. A
RAT is typically installed without the victim’s knowledge. - HTTP (Hypertext Transfer Protocol )
HTTP is an application protocol for distributed, collaborative, and hypermedia information systems. HTTP is the foundation of data communication for the World Wide Web and bots are controlled through webpanel. This type of botnet is widely used along with other types too.
We will learn about setting up RAT and HTTP botnets in our next post. But today let’s learn about some requirements for those botnets. This will help you to make a mindset and make you easy with the requirements and you can keep up with the tutorial without getting errors.
Read our previous article on how to use darknet
What are the requirements for RAT?
You can use the Remote Administration Tool(RAT) either paid or free. It’s upon you but I will provide some information on RAT which is paid and free.
These are some of the free RAT
- Quasar
- Babylon
- Darktrack
- Njrat
This is an example of a cracked RAT
- Nanocore
These are some of the paid RAT
- Netwire
- Imminent Monitor
- Orcus
- Remcos
Another required thing is Crypters
Crypters are legal encrypting tools. If used correctly, and with proper permission, then you have nothing to worry about. On the other hand, if you are using crypters to encrypt malware with the sole purpose of infecting computers that are not yours you are committing a crime. When it comes to crypters it’s a whole series of choices. I will explain to you how to use crypter in our next article.
- Another requirement is a Domain Name System(DNS)
DNS is a hierarchical decentralized naming system for computers, services, or other resources connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities. It translates more readily memorized domain names to the numerical IP addresses needed for locating and identifying computer services and devices with the underlying network protocols. By providing a worldwide, distributed directory service, the Domain Name System is an essential component of the functionality on the Internet. It has been in use since 1985.
Virtual private network (VPN) is also a requirement for RAT
A virtual private network extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running across the VPN may therefore benefit from the functionality, security, and management of the private network.
What are HTTP C&C Requirements
These are some if the requirements for setting up a botnet using http.
- VPS (Virtual Private Server)
- Domain Name
- Crypter
- Botnet webpanel files, builder or build connected to your domain/server IP
This is the end for the first part of our what is a botnet and some information about botnet. We learn about botnets, types of botnets, and examples of RAT. If you have any queries then feel free to contact us.





Daniel
Hey. A great article. Unfortunately, all the time 90% of computer users are not aware of the threat. Honestly? I think that every day when logging into the network, large IT corporations, social networking sites etc use botnet “technology” and make money from it. Such times … The next part I propose to do about fighting, ways to secure your network against Botnet 🙂 . Greetings!!
Roshan
Thank you for your feedback. I will soon write article on it. Thank you so much 😊